At 6 AM, Emma’s phone rang. Her flower shop’s computer system was frozen, displaying: “Pay $5,000 or lose everything.” Three days of Valentine’s orders vanished; customer addresses and payment records were held hostage.
Emma isn’t alone. Do you know how many cyber attacks happen per day? 2,200. Every 39 seconds, hackers target another small business: the bakery down your street, your family dentist, your neighborhood bookstore.
You built your business to serve customers, not battle cybercriminals. Recent cyber attacks demonstrate how cybercriminals increasingly target small businesses they perceive as easy prey.
That’s why every business needs a proactive cybersecurity program, and as a cybersecurity services provider, we can help.
Cybersecurity program development for business starts with knowing your enemies. Phishing emails steal passwords. Ransomware locks files for ransom. Insider threats emerge when trusted employees make costly mistakes.
Today’s threats evolve rapidly. AI powers smarter attacks. Cloud systems create new vulnerabilities. Stricter regulations demand customer data protection or impose heavy penalties.
Small businesses need tailored cybersecurity programs, not enterprise solutions. This guide provides step-by-step instructions for building an effective cybersecurity strategy that protects your business, customers, and livelihood without breaking your budget.
What is a Cybersecurity Program?
A cybersecurity program is a set of coordinated activities, policies, and controls designed to protect your business data, systems, and reputation from cyber threats. It also helps you recover quickly if an incident occurs.
The importance of cybersecurity program becomes clear when you consider three key goals for your business assets:
Why Cybersecurity Program Development is Critical for Modern Businesses?
Here’s why you need a cybersecurity program development plan:
Your approach doesn’t need to be complex. Simple cybersecurity program management with basic access control and a clear governance framework can protect what matters most.
What’s Actually Worth Protecting in Your Business?
Here’s the truth: You can’t protect everything equally. And you shouldn’t try.
Think about it this way – if everything vanished tomorrow, what would actually cripple your business? Your customer list? Access to bank accounts? Your payroll system? The answer isn’t the same for everyone.
Your Simple Asset Protection Worksheet
Grab a pen and answer these questions honestly:
Most small businesses have just 3-5 truly critical assets. Focus there first.
The Five Decisions That Actually Matter
Every cybersecurity program development framework starts with these core questions:
“I’ve seen companies waste thousands on fancy tech before answering these basic questions. Get clarity first, then build your cybersecurity program.” – Mayur Panchal CTO, Excellent Webworld
How Do You Make Your Cybersecurity Program for Business in 7 Steps
Now that you understand your risks and have decided your priorities, here’s how to build your program step by step:
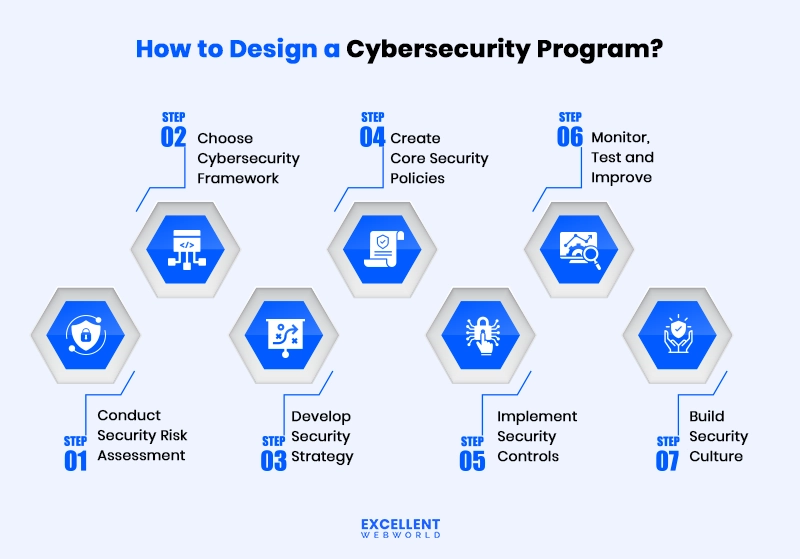
Let’s get into the nitty-gritty of each step in the upcoming sections.
Step 1: Conduct a Security Risk Assessment (The Right Way)
Your risk assessment isn’t just another checkbox exercise. It’s your roadmap for making smart security decisions with limited resources.
Most businesses skip this step and jump straight to buying tools. A proper assessment shows you where to spend your limited budget for maximum protection.
Your Simple 3-Step Assessment Process
1. Map Your Digital Assets
2. Identify Real Threats
3. Spot Your Weak Points
Legal Requirements You Can’t Ignore
Different industries have different rules. Healthcare needs HIPAA-compliant app development, while banking/finance applications need to follow PCI-DSS standards.
Your cybersecurity program manager must understand which regulations apply to your business.
Security compliance isn’t optional – it’s often legally required and affects insurance coverage.
Tools That Actually Help
Start with these free resources:
But honestly? A simple spreadsheet works best when you’re starting.
Create three columns: “What We Have,” “Risk Level,” and “Action Needed.” Track your computers, data, and access points here.
Your security architecture can grow as your business does. Don’t overcomplicate it with fancy tools that require a SOC as a Service to manage the complexity.
Step 2: Choose the Right Cybersecurity Framework for Your Business
You need a roadmap. That’s what cybersecurity frameworks give you: a clear plan to protect your business without getting lost in tech talk.
The three main cybersecurity frameworks are:
Why Frameworks Matter for Small Businesses?
You don’t have time to guess what security you need. Frameworks show you exactly where to start and what comes next.
They help you focus your limited budget on what actually protects your business. No more wondering if you’re missing something critical.
How to Make These Frameworks Work for Small Businesses?
Start with the basics:
Add cloud security measures as you grow. Implement DevSecOps practices when you have dedicated IT staff.
When Frameworks Help vs. Hurt?
As a CTO, I’ve seen frameworks become paperwork nightmares for small teams. Use them as guides, not rigid rules.
Focus on cybersecurity program best practices that fit your reality. Track simple cyber security KPIs, like how many employees completed security training.
Skip the complex parts until you master the basics. Your customers care more about their data being safe than your compliance certificates.
Step 3: Develop a Business-Aligned Cybersecurity Strategy and Team
Your cybersecurity plan must match your business needs. Don’t build a fortress when you need a fence.
Align Security with Your Business Goals
Start by listing what matters most to your business. Is it customer data? Financial records? Daily operations? Your security efforts should protect these priorities first.
If you run an online store, focus on payment security. If you handle medical records, prioritize data protection.
Create a simple roadmap:
Define Clear Roles and Responsibilities
Every team member needs to know their security duties.
Assign these basic roles:
Your disaster recovery plan should be simple. Write down how to restore key systems and who does what.
Make sure everyone knows who to call when something goes wrong. Clear roles prevent confusion during emergencies.
Build Your Security Team
You have three main options when starting cybersecurity program development and management:
For most small businesses, outsourced or managed services offer the best value. You get expert knowledge without full-time salaries.
Step 4: Create Core Security Policies That Work in Real Life
You need policies that your team will actually follow. Not 50-page documents that sit in a drawer.
The Three Must-Have Policies
Acceptable Use Policy – This tells your team what they can and cannot do with company computers and the internet. Keep it simple:
Access Controls – Who can see what in your business? This prevents insider mistakes:
Remote Work Policy – With employees working from home, you need clear rules:
Keep It Simple and Enforceable
As a CTO of a top-rated cybersecurity services provider company, I’ve seen businesses create policies nobody reads.
Essential Training That Actually Works
Your Security Information and Event Management System (SIEM) and firewall management tools mean nothing if employees click on malicious links.
Step 5: Implement Practical, Affordable Security Controls
You don’t need expensive threat intelligence tools for cyber attack prevention. Simple security cybersecurity tips for small businesses block 90% of threats.
Start With These Five Must-Have Controls
2025 Security Trends You Need to Know
Discover the essential cybersecurity trends transforming how organizations defend against sophisticated digital threats in 2025.
Client Success Stories: How Small Changes Made a Big Difference?
Maria’s bakery received 50+ supplier emails daily during the holiday season. She feared malware would ruin Christmas orders. We implemented code review checks. Last December, it fell victim to ransomware in a fake invoice. This time, Maria saved her $40,000 holiday revenue.
Jake’s auto shop processed 200 online payments monthly but lacked security expertise. Customers complained about slow checkout. We deployed Dynamic Application Security Testing (DAST), and it found credit card vulnerabilities before hackers did. Customer complaints dropped 80%.
Step 6: Ongoing Monitoring, Testing, and Continuous Improvement
Your cybersecurity program isn’t a “set it and forget it” solution. You need to keep testing and improving it regularly.
Why Continuous Assessment Matters?
Regular assessment helps you catch problems before they become disasters. Here’s what you should do:
Your CISO (Chief Information Security Officer) or security consultant should guide these activities. Even small businesses benefit from this expertise.
What Our CTO Says About Realistic Expectations?
Based on our consulting experience with 200+ small businesses, here’s what I advice:
How to Measure Your Success?
Track these simple numbers monthly:
Consider starting a bug bounty program where ethical hackers help find weaknesses. Many software platforms now offer this affordably.
Keep records for forensic analysis if something goes wrong. This helps you learn and improve faster.
Step 7: Building a Security Culture That Lasts
Your cybersecurity is only as strong as your people. That’s why building a security culture matters more than any software you buy.
Make Security Everyone’s Job
Security isn’t just your IT person’s responsibility. It starts with you as the leader.
When your newest employee sees you taking security seriously, they will too.
Simple Security Training That Works
Skip the boring hour-long presentations. Your team needs practical training they can use right away.
Keep Your Team Engaged
Make security training something your team actually wants to do.
Track Your Progress
Use a simple maturity assessment to see how your security culture grows over time.
If You’re Feeling Overwhelmed, Here’s What To Do First
Stop. Take a deep breath. You’re not broken.
Every smart business owner feels this way when they start thinking about security. I see it daily in my consulting work.
Here’s your relief: You don’t need to become a security expert today.
Do these three things right now:
Done. You just did more than most businesses ever do.
Pick one thing tomorrow. Fix only that. Then reward yourself with coffee. You’re already ahead of competitors who ignore this completely.
Modern cloud solutions and AI-powered security tools will actually simplify this process later. But these baby steps matter most right now.
Excellent WebWorld for Cybersecurity Program Development
Look, I’ve been in tech long enough to see what really happens to small businesses when cyber attacks hit.
It’s not pretty. And it’s happening more often than you think.
But here’s what most people don’t tell you – You shouldn’t have to become a cybersecurity expert to protect your business. You just need someone who actually gets what small businesses face every day.
Most vendors want to sell you complicated systems you’ll never understand. We want to give you peace of mind without the headache.
Here’s How We Make Cybersecurity Simple for You:
We’ve seen too many small businesses suffer because they waited too long or chose the wrong approach.
Don’t let that be you.
Ready to protect what you’ve built? Schedule your free security assessment today. Let’s make your business hacker-proof together.
FAQs About Cybersecurity Program Development for SMBs:-
Cyberattacks can destroy your business by stealing customer data, draining bank accounts, and shutting down operations. Small businesses often can’t recover from major cyber incidents, with 60% closing within six months of an attack.
Yes, small businesses are heavily targeted because hackers see them as easy targets with weaker security. Over 40% of cyberattacks target small businesses, and the frequency is increasing every year.
The biggest threats are phishing emails, ransomware that locks your files, password attacks, and malware infections. These account for most successful attacks against small businesses.
Start with anything connected to the internet: computers, phones, email, customer data, and financial information. Also consider physical access to your office and backup systems.
Not necessarily. Many small businesses start with basic security tools and managed services. You can outsource cybersecurity to specialists rather than hiring full-time staff.
Use strong, unique passwords with a password manager, enable two-factor authentication, keep software updated, and train employees to spot phishing emails. Back up your data regularly.
The cost varies greatly, but generally falls between $10,000 and millions of dollars annually, depending on size and complexity. Small businesses might spend $10,000-$100,000, while larger enterprises could invest millions. A good rule of thumb is to allocate 7-10% of your IT budget to cybersecurity.
Consider managed cybersecurity services that handle protection for you. Many providers offer affordable packages for small businesses, so you don’t need internal expertise or time.

Article By
Mayur Panchal is the CTO of Excellent Webworld. With his skills and expertise, He stays updated with industry trends and utilizes his technical expertise to address problems faced by entrepreneurs and startup owners.



